As online shopping has continued to grow exponentially, so too have opportunistic cybercriminals looking to exploit vulnerabilities for financial gain. eCommerce fraud now costs businesses billions of dollars every year. To help combat this rising threat, many companies have begun implementing artificial intelligence-based fraud detection systems.
These advanced AI solutions analyze massive troves of transaction data using sophisticated machine learning algorithms.
By examining patterns in areas like payment details, device and location information, and shopping behaviors, the systems can identify suspicious activity that may indicate fraudulent purchases or accounts. They also have the advantage of continuously learning and improving over time as they process more legitimate and fraudulent transactions.
The implementation of AI fraud detection represents a significant evolution from traditional rule-based approaches that were less adaptable.
For ecommerce businesses aiming to protect themselves and their customers in the digital age, these new AI-powered security solutions have shown great potential to help curb losses and build trust in the online shopping experience.
Understanding AI-Powered Fraud Detection in eCommerce
Modern eCommerce fraud detection systems employ advanced computational methods to sift through massive amounts of transaction data. Machine learning has fundamentally transformed how businesses protect themselves against increasingly sophisticated fraud attempts that cost the global economy billions of dollars annually.
How machine learning models detect fraud patterns
Machine learning fraud detection operates through a systematic process that begins when a user interacts with an ecommerce platform. The technology collects data about the interaction device information, IP address, location, and shopping behavior.
Subsequently, algorithms analyze this data using two primary approaches:
- Supervised learning examines historical behavioral patterns to predict outcomes of current interactions. This method studies past loan repayments, dispute history, and refund requests to identify potential fraud.
- Unsupervised learning analyzes current attributes to detect anomalies without predefined labels, enabling the system to identify novel fraud tactics independently.
After analysis, the system determines risk levels, consults business policies, and takes appropriate action, blocking, accepting, or flagging interactions for review. Notably, these systems continuously learn from each transaction, improving accuracy over time.
Role of behavioral analytics in ecommerce security
Behavioral analytics combines machine learning with big data analysis to examine user actions and identify suspicious patterns. This approach creates detailed profiles of normal behavior, making it easier to spot deviations that may indicate fraudulent activity.
For instance, behavioral analysis might flag a transaction as suspicious if a customer who typically makes small purchases suddenly orders an expensive item from an unusual location. Another example would be detecting impossible travel scenarios, like purchasing coffee in Los Angeles and then making another purchase in London 20 minutes later.
This technology examines numerous behavioral indicators:
- Typing patterns and keyboard dynamics
- Mouse movements and navigation habits
- Time-of-day usage patterns
- Transaction frequency and amounts
- Geographic location patterns
Companies like Amazon have achieved market dominance partly through analyzing both browsing and buying habits, creating effective customer segmentation that improves both security and personalization.
Moreover, Mastercard’s Identity Engine utilizes behavioral analytics to calculate real-time risk scores on a scale of 0-500, with higher numbers indicating riskier transactions.
Difference between rule-based and AI-based systems
Traditional rule-based fraud detection relies on predefined criteria programmed by humans, essentially “if X, then do Y” logic. While effective against known fraud patterns, these systems struggle with adaptability.
Once fraudsters discover the rules, they can modify their techniques to bypass detection.
Conversely, AI-based systems take a probabilistic approach, considering hundreds of variables before deciding whether a transaction is fraudulent.
Instead of following static rules, these systems:
- Continuously adapt to new fraud tactics
- Process large datasets with multiple variables
- Identify subtle correlations human analysts might miss
- Reduce false positives by approximately 70% while maintaining high fraud detection rates
Despite these advantages, organizations often benefit from combining both approaches. Rule-based systems offer transparency and control, whereas AI systems provide adaptability and pattern recognition.
This hybrid approach allows businesses to leverage the strengths of each methodology using explicit rules for known fraud patterns while employing machine learning to detect novel threats.
External Threats AI Can Detect in Online Stores
External cyber threats targeting online stores have grown increasingly sophisticated, requiring advanced AI detection capabilities to identify and neutralize attacks before they compromise customer data or business operations. The retail industry experiences the highest volume of attacks, with 569,884 AI-driven attacks occurring daily.
Phishing and social engineering detection using NLP
Natural Language Processing (NLP) technologies analyze linguistic patterns, sentiment fluctuations, and contextual anomalies to detect deceptive communication in emails, messages, and other digital interactions. AI-powered phishing detection examines suspicious messages in real-time, even before sensitive information can be entered.
Modern NLP systems utilize transformer-based models like BERT and GPT to recognize complex language features that indicate deception, including inconsistencies, emotional manipulation, and subtle threats embedded in communications.
According to Visa’s Biannual Threat Report, fraudsters increasingly use generative AI to create well-crafted phishing campaigns, deep fake dating profiles, and voice cloning to impersonate trusted contacts.
In practical applications, NLP analyzes distinct indicators invisible to human users to determine when a webpage isn’t what it appears to be.
Notably, NLP-based models significantly outperform traditional rule-based detection systems, particularly for sophisticated attacks that use OTP workflows, payment forms, and non-traditional credential harvesting methods.
Real-time malware and ransomware pattern recognition
AI systems detect ransomware through advanced pattern recognition that identifies unusual behavior before encryption begins.
According to brand phishing statistics in early 2024, Microsoft was the most frequently impersonated brand by cybercriminals attempting to trick people, accounting for 38% of all phishing scams reported. Google came in second place, making up approximately 11% of total phishing attempts during that same time period.
Criminals increasingly leverage AI tools to improve attack effectiveness through several methods:
- Generating polymorphic ransomware strains that constantly modify code
- Optimizing delivery mechanisms using machine learning
- Analyzing large datasets to identify potential targets and vulnerabilities
These AI-enhanced threats are evolving quickly, with predictions that large language models will soon be offered as Ransomware as a service (RaaS) to deploy attacks more efficiently.
Correspondingly, defensive AI systems must continuously learn from each new threat, incorporating real-time analysis to identify attack patterns before data exfiltration occurs.
SQL injection and XSS detection with anomaly models
SQL injection attacks remain one of the most prevalent cyberattacks targeting web-based applications. These attacks typically manipulate input fields by adding unauthorized characters or commands to SQL queries, allowing attackers to bypass authentication protocols.
Similarly, Cross-Site Scripting (XSS) attacks have been listed by the Open Web Application Security Project (OWASP) as a top web application security risks. AI-based anomaly detection models analyze SQL query sequences to identify unusual patterns that may indicate an injection attempt.
Advanced machine learning models including LSTM, CNN, and boosting algorithms like AdaBoost have proven highly effective in detecting these attacks. Random Forest methods have achieved performance ratings of 0.99, outperforming other approaches in identifying XSS vulnerabilities.
Bot attack mitigation using behavioral biometrics
Behavioral biometrics provides continuous authentication by analyzing how individuals interact with devices, from keystroke dynamics and mouse movements to tap pressure and navigation patterns. This technology creates a unique behavioral profile that’s extremely difficult for bots to spoof.
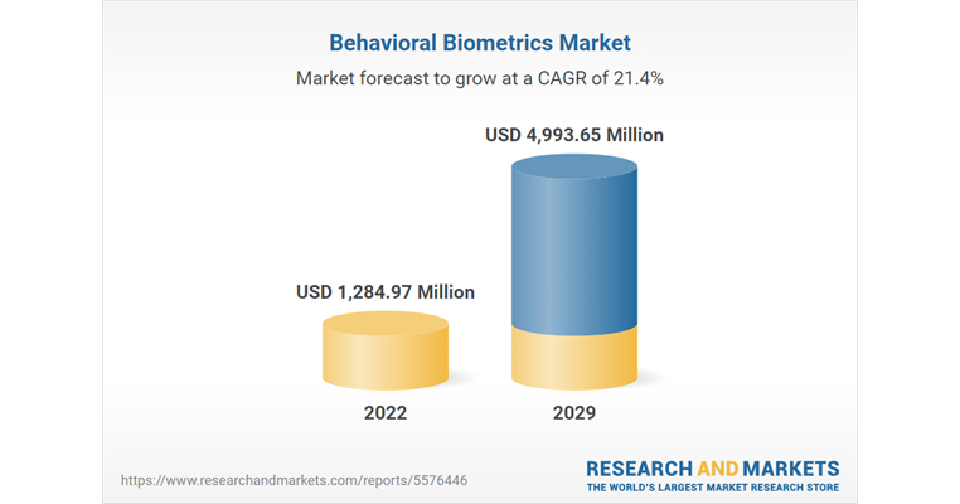
The technology examines thousands of micro-patterns, including scroll velocity, typing pace, and hesitation while entering data, to distinguish between legitimate users and automated bots. The market for behavioral biometrics is expected to grow at a CAGR of 21.4% to reach a market size of US$4,993.653 million by the year 2029.
Retail experiences the highest volume of bot attacks, with scalping bots targeting any industry where demand outstrips supply. These sophisticated programs cost businesses up to $48 billion annually in fraud losses, necessitating multi-layered protection including API security, bot fingerprinting, and proactive monitoring.
E-skimming and card-not-present fraud detection
Digital skimming (e-skimming) targets online stores by embedding malicious code that steals payment credentials.
According to Mastercard data, nearly three-quarters of publicly disclosed breaches in 2022 involved digital skimming, with 4,500 new sites infected, a 129% increase from 2021. The FBI estimates these scams now cost cardholders and banks over USD 1.00 billion every year.
Concurrently, Card-Not-Present (CNP) fraud involves unauthorized transactions where physical cards aren’t present.
Globally, CNP fraud losses are estimated to reach $28 billion by 2026, a 40% increase from 2023. AI detection systems analyze multiple indicators including device fingerprinting, address verification, and behavioral patterns to identify suspicious transactions.
Customers who transact at infected merchants are more likely to become victims of fraud. Fortunately, AI-powered fraud detection systems can analyze dozens of risk factors simultaneously, reducing fraud losses for major retailers.
Internal Risks and How AI Helps Prevent Them
Internal security breaches pose a significant challenge for eCommerce businesses, with 60% of data breaches attributed to insider threats. These internal vulnerabilities often go undetected longer than external attacks, making AI-powered detection systems increasingly vital for comprehensive security strategies.
Detecting insider threats through access pattern monitoring
AI systems excel at analyzing user access patterns to identify suspicious behavior that may indicate malicious intent. These solutions establish baseline patterns of normal user behavior and flag deviations that might signal potential threats. For instance, if an accounting employee who typically accesses financial records during business hours suddenly downloads large volumes of customer data at 2 AM, AI would immediately flag this activity despite valid credentials.
Advanced monitoring systems analyze thousands of data points including:
- Access timing and frequency
- Volume of files accessed
- Geographic location patterns
- Typing patterns and mouse movements
Data security experts have demonstrated that analyzing user access patterns stored in database logs effectively detects anomalous events through user pattern analysis, machine learning, and rule-based access control.
Preventing employee negligence with AI-based alerts
Beyond malicious intent, employee negligence represents a significant security risk. AI-based systems help prevent accidental data exposure through real-time monitoring and alerts. These tools can detect concerning activities like “sweethearting” when employees give products to friends without charging them or bill for cheaper items than those purchased.
AI-enabled compliance monitoring continuously audits employee activities, financial transactions, and other risk areas, automatically flagging policy violations. This proactive approach allows security teams to address potential issues before they escalate into significant problems. Additionally, AI reduces false positives by approximately 80%, enabling security personnel to focus on genuine threats rather than investigating false alarms.
Third-party risk scoring using graph neural networks
Third-party vendors often represent significant security vulnerabilities for eCommerce platforms. AI systems utilizing graph neural networks analyze complex relationships between organizations and their partners to identify potential risks. These networks examine connections, dependencies, and historical interactions to generate comprehensive risk scores.
AI enables customizable risk models tailored to specific organizational needs, moving beyond traditional one-size-fits-all approaches. These systems continuously evaluate third-party relationships, automatically adjusting risk scores based on changing conditions and newly identified threats. Furthermore, AI-powered risk scoring allows for dynamic authentication that adapts based on risk assessment, escalating security requirements when unusual patterns are detected.
Best Practices for Implementing AI in eCommerce Security
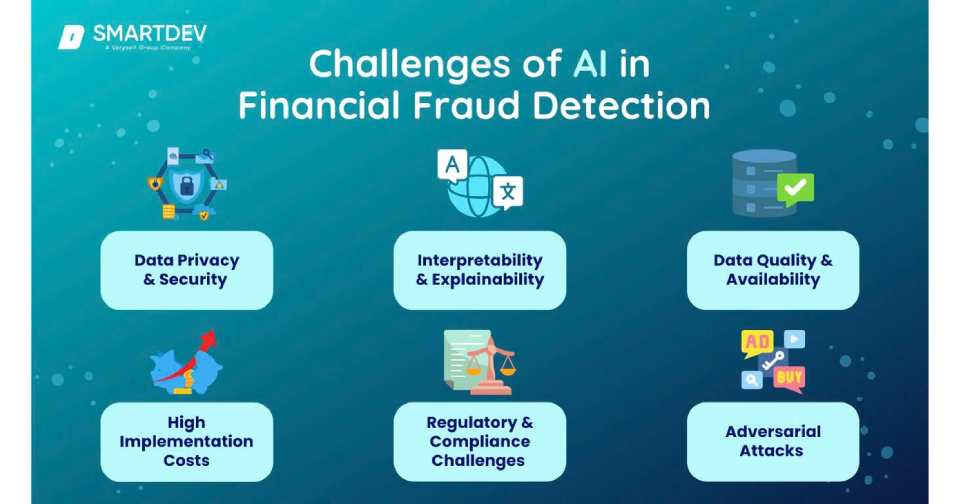
Successful implementation of AI security solutions requires strategic planning and precise execution to maximize protection while maintaining smooth customer experiences. Effective deployment focuses on integration, monitoring, and continuous refinement.
Integrating AI with existing fraud prevention systems
Implementing AI as part of a multi-layered security approach yields optimal results. Traditional fraud prevention systems often rely on binary approve/decline decisions, whereas AI integration enables adaptive responses based on risk levels. Organizations should begin with targeted AI pilots in specific departments before scaling to the entire operation. A hybrid approach combining legacy systems with AI-driven models significantly improves fraud detection accuracy while reducing response time. This integration allows businesses to leverage both rule-based systems for transparency and AI for pattern recognition, creating a comprehensive defense mechanism.
Using device fingerprinting and behavioral biometrics
Device fingerprinting creates unique digital signatures by analyzing hardware, software, and network characteristics. This technology works seamlessly in the background, authenticating users without disrupting their experience. When combined with behavioral biometrics, which examines typing patterns, mouse movements, and touch gestures, merchants can build detailed user profiles that are extremely difficult to falsify. These technologies reduce false positives by up to 50 times more effectively than cookies, ensuring legitimate users aren’t inconvenienced while effectively filtering out fraudulent transactions.
Real-time risk scoring at checkout
Adaptive checkout processes customize security measures based on transaction risk profiles. Riskified’s system intelligently routes orders through specific flows, selectively applying additional verification like CVV confirmation or one-time passwords only when necessary. This approach minimizes disruption for legitimate customers while effectively blocking fraud at various stages. Advanced configurations can even screen out blatant fraud before it reaches the issuer’s authorization checks.
Training AI models with ecommerce-specific datasets
AI models perform best when trained with relevant, high-quality data. Effective training requires datasets that include both legitimate transactions and identified examples of fraudulent behavior. Models should continuously learn from each new transaction, improving accuracy over time. Primarily, organizations should prioritize data freshness, since stale information leads to outdated pattern recognition in rapidly evolving fraud landscapes.
Compliance and Ethical Considerations for AI Use

Regulatory frameworks increasingly shape how AI-powered fraud detection systems operate in eCommerce environments. Organizations must balance effective security measures with ethical considerations and compliance requirements to avoid severe penalties.
Ensuring GDPR and CCPA compliance in AI models
AI fraud detection systems processing customer data must adhere to key privacy regulations. Under GDPR, organizations need explicit consent when using personal information to train AI models. The California Consumer Privacy Act (CCPA) similarly grants consumers rights regarding data collection and automated decision-making. To maintain compliance, businesses should:
- Implement data minimization principles, collecting only information necessary for fraud detection
- Provide clear privacy notices explaining AI usage in fraud prevention
- Establish mechanisms for consumers to access, delete, and opt out of AI processing
The CCPA specifically requires organizations to perform risk assessments before using automated decision-making technology for significant decisions. Furthermore, when AI models contain personal data, they cannot be considered anonymous as they’re designed to provide outputs based on training information.
Explainable AI for audit trails and transparency
The “black box” nature of AI systems creates significant challenges for regulatory compliance. Explainable AI (XAI) techniques help organizations provide understandable reasons for fraud flags while supporting transparent decision-making. This transparency enables:
- Clear audit trails documenting system decisions
- Meaningful explanations of how fraud determinations are made
- Enhanced trust among customers and regulators
Techniques like SHAP (SHapley Additive exPlanations) and LIME (Local Interpretable Model-agnostic Explanations) deliver local and global interpretability, creating verifiable explanations for AI decisions. Consequently, when fraud alerts are triggered, businesses can explain precisely which factors contributed to the determination.
Avoiding bias in fraud detection algorithms
Bias in AI fraud detection can lead to discriminatory outcomes and legal liabilities. Historical human biases often infiltrate algorithms through training data, potentially resulting in harmful consequences. Multiple approaches exist for mitigating unfairness:
- Demographic Parity ensures equal probability of fraud prediction across different groups
- Equalized Odds maintains consistent probability selection regardless of sensitive attributes
- Predictive Rate Parity ensures consistent outcome prediction across different groups
Nevertheless, these fairness concepts are mutually exclusive; organisations must select one approach and accept trade-offs between accuracy and fairness. Organisations should regularly monitor AI systems to track their impact on diverse customer groups and make adjustments when biases emerge.
The Future of AI-Powered Fraud Protection
AI-powered fraud detection systems have fundamentally transformed eCommerce security landscapes. Throughout this article, we explored how machine learning models analyze vast transaction datasets to identify fraudulent patterns, often detecting threats within milliseconds. Additionally, behavioral analytics creates detailed user profiles that make suspicious activities immediately apparent to security systems.
The distinction between traditional rule-based systems and AI-based detection represents a critical evolution. While rule-based approaches follow static guidelines, AI systems adapt continuously, learning from each transaction to improve accuracy. Consequently, businesses implementing hybrid approaches benefit from both the transparency of rules and the pattern recognition capabilities of artificial intelligence.
External threats, including phishing, ransomware, SQL injection, bot attacks, and e-skimming require sophisticated detection mechanisms. Likewise, internal risks from employee negligence and third-party vulnerabilities demand equally robust prevention strategies. AI excels at identifying both categories of threats through continuous monitoring and analysis.
Best practices for implementation involve strategic integration with existing systems, comprehensive device fingerprinting, real-time risk scoring, and training models with relevant datasets. Nevertheless, these technological capabilities must balance with ethical considerations and regulatory compliance requirements, including GDPR and CCPA.
Conclusion
The financial stakes remain significant. Though cybercriminals increasingly leverage AI to enhance their attacks, defensive AI systems offer robust countermeasures, potentially reducing fraud losses by approximately 80% for major retailers. Success stories from companies like American Express and PayPal demonstrate the tangible benefits of AI-powered security solutions.
Undoubtedly, as eCommerce continues growing, AI-powered security will become standard rather than optional. Businesses that implement these technologies effectively not only protect their bottom line but also build customer trust through reliable security measures. The evolutionary race between fraudsters and security systems continues, but AI provides businesses with unprecedented capabilities to stay ahead of emerging threats.
Acowebs are the developers of the WooCommerce Product Labels which let customers include custom product labels or product badges for the WooCommerce products. WooCommerce sales badges plugin provides you with different label styles and customizations for labels. It offers a easy-to-use UI to add labels to the selected products or categories and woocommerce email customizer using which you can easily build and customize WooCommerce emails with a drag-and-drop user interface.












 Login
Login
 Cart
Cart







